- Remote Desktop Protocol For Windows 7
- Remote Desktop Protocol Windows 7 Download
- Remote Desktop Protocol Download
In computing, the term remote desktop refers to a software or operating system feature that allows a personal computer's desktop environment to be run remotely on one system (usually a PC, but the concept applies equally to a server), while being displayed on a separate client device. Remote desktop applications have varying features. Some allow attaching to an existing user's session (i.e., a running desktop) and 'remote controlling', either displaying the remote control session or blanking the screen. Taking over a desktop remotely is a form of remote administration.
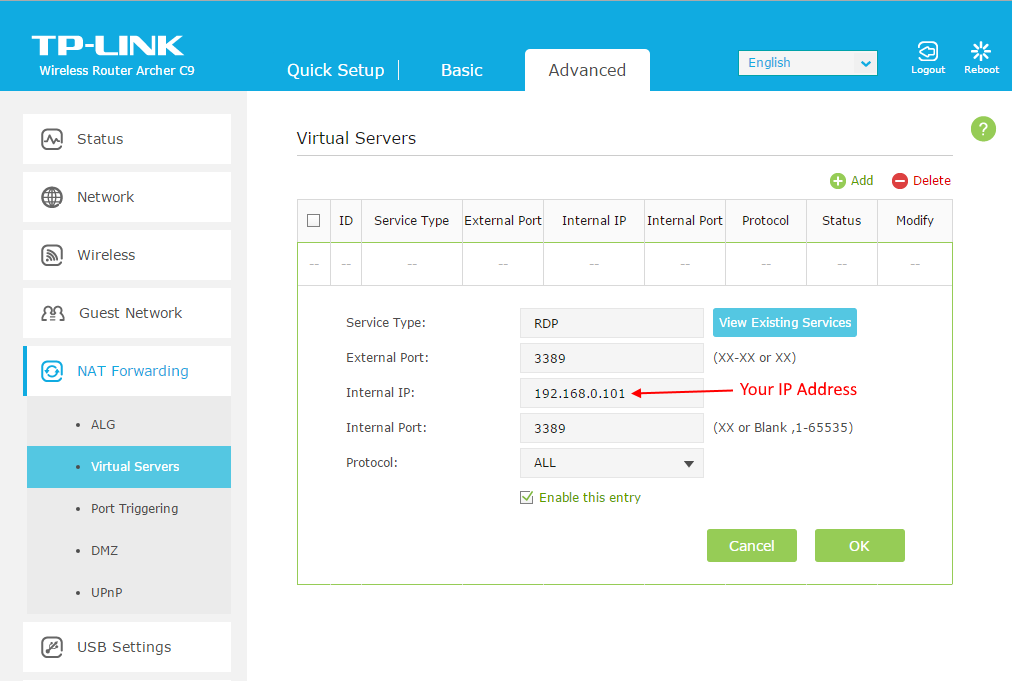
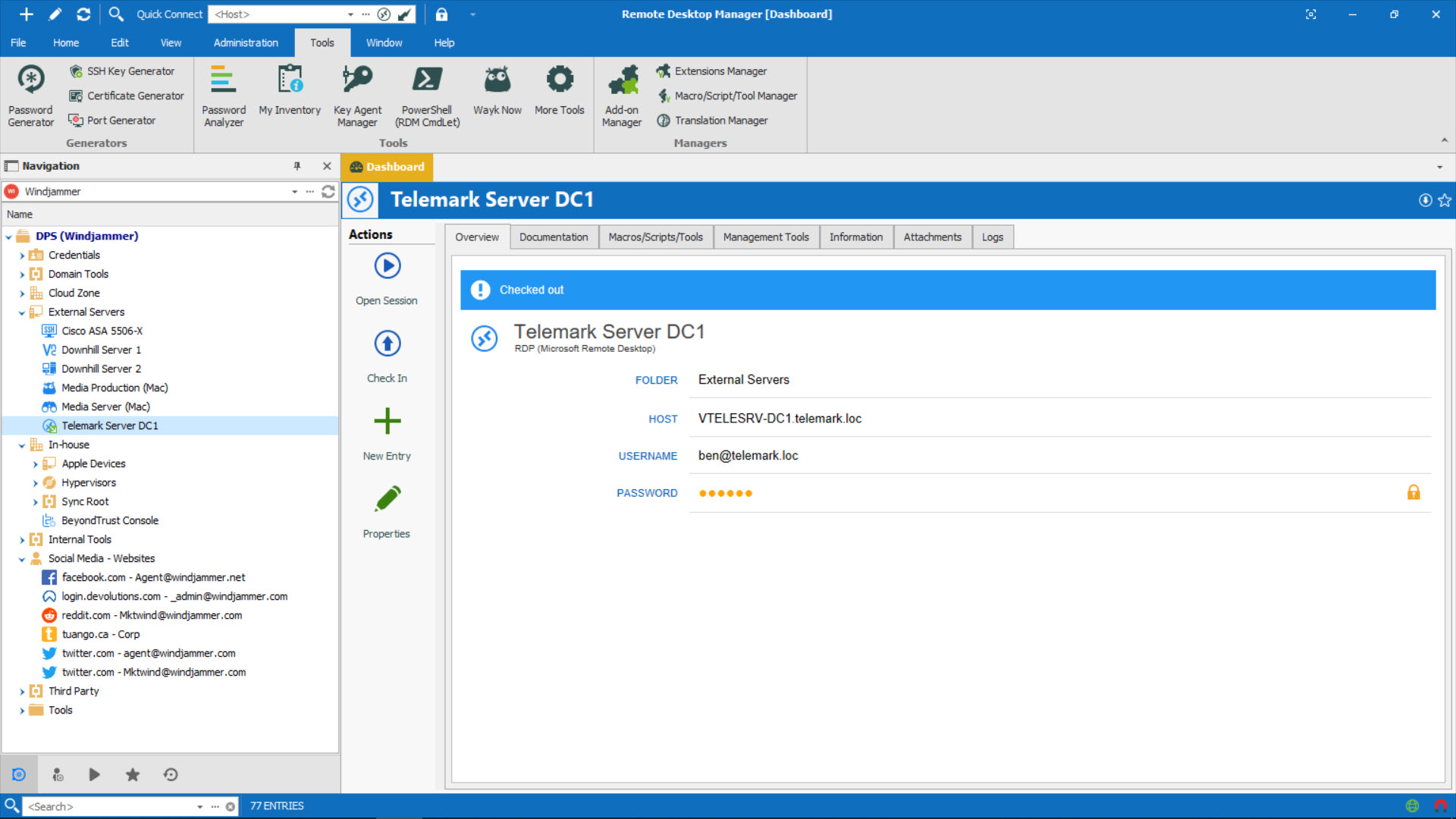
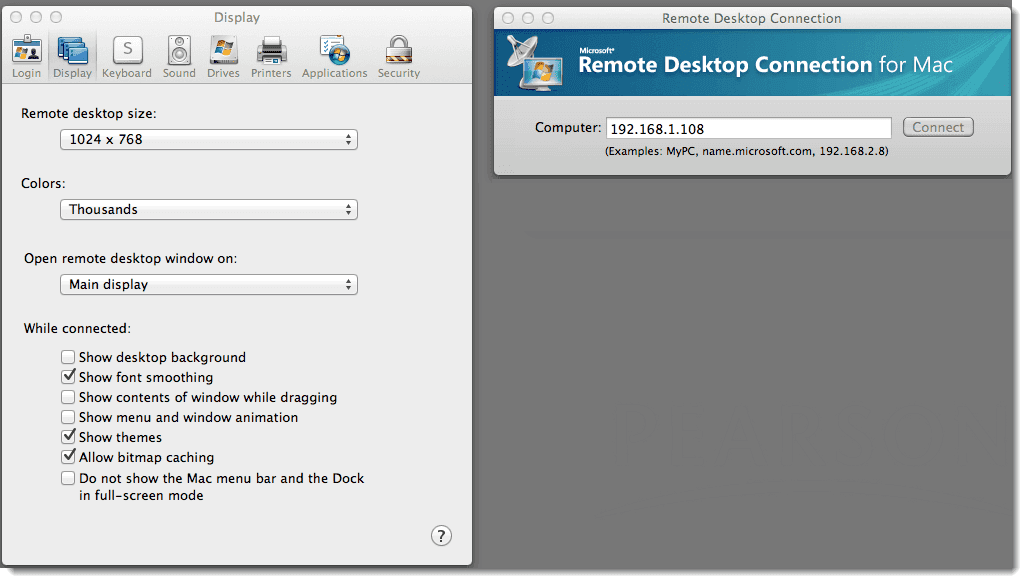
Use sc cmd to get running services on the remote server. Make sure you can use windows explorer to access the remote server remoteserver. Sc remoteserver query. Find out the service you can stop. Sc remoteserver stop After stopping one service, the remote desktop works again. Remote Desktop Protocol (RDP) is a sophisticated technology that uses various techniques to perfect the server's remote graphics' delivery to the client device. Depending on the use case, availability of computing resources, and network bandwidth, RDP dynamically adjusts various parameters to deliver the best user experience.
Overview[edit]
Remote access can also be explained as remote control of a computer by using another device connected via the internet or another network. This is widely used by many computer manufacturers and large businesses help desks for technical troubleshooting of their customer's problems.
Remote desktop software captures the mouse and keyboard inputs from the local computer (client) and sends them to the remote computer (server).[1] The remote computer in turn sends the display commands to the local computer. When applications with many graphics including video or 3D models need to be controlled remotely, a remote workstation software that sends the pixels rather than the display commands must be used to provide a smooth, like-local experience.
Remote desktop sharing is accomplished through a common client/server model. The client, or VNC viewer, is installed on a local computer and then connects via a network to a server component, which is installed on the remote computer. In a typical VNC session, all keystrokes and mouse clicks are registered as if the client were actually performing tasks on the end-user machine.[2]
The target computer in a remote desktop scenario is still able to access all of its core functions. Many of these core functions, including the main clipboard, can be shared between the target computer and remote desktop client.
Uses[edit]
A main use of remote desktop software is remote administration and remote implementation. This need arises when software buyers are far away from their software vendor. Most remote access software can be used for 'headless computers': instead of each computer having its own monitor, keyboard, and mouse, or using a KVM switch, one computer can have a monitor, keyboard, mouse, and remote control software, and control many headless computers. The duplicate desktop mode is useful for user support and education. Remote control software combined with telephone communication can be nearly as helpful for novice computer-users as if the support staff were actually there.
Since the advent of cloud computing remote desktop software can be housed on USB hardware devices, allowing users to connect the device to any PC connected to their network or the Internet and recreate their desktop via a connection to the cloud. This model avoids one problem with remote desktop software, which requires the local computer to be switched on at the time when the user wishes to access it remotely. (It is possible with a router with C2S VPN support, and Wake on LAN equipment, to establish a virtual private network (VPN) connection with the router over the Internet if not connected to the LAN, switch on a computer connected to the router, then connect to it.)
Remote desktop products are available in three models: hosted service, software, and appliance.
Tech support scammers use Remote Desktop software to connect to their victim's computer and will often Syskey the computer if the victim does not cooperate.
Protocols[edit]
Remote desktop protocols include the following:
- Apple Remote Desktop Protocol (ARD) – Original protocol for Apple Remote Desktop on macOS machines.
- Appliance Link Protocol (ALP) – a Sun Microsystems-specific protocol featuring audio (play and record), remote printing, remote USB, accelerated video
- HP Remote Graphics Software (RGS) – a proprietary protocol designed by Hewlett-Packard specifically for high end workstation remoting and collaboration.
- Independent Computing Architecture (ICA) – a proprietary protocol designed by Citrix Systems
- NX technology (NX) a proprietary protocol designed by NoMachine with open-source derivatives available from other forked projects.
- PC-over-IP (PCoIP) – a proprietary protocol used by VMware (licensed from Teradici)[3]
- Remote Desktop Protocol (RDP) – a Windows-specific protocol featuring audio and remote printing
- Remote Frame Buffer Protocol (RFB) – A framebuffer level cross-platform protocol that VNC is based on.
- SPICE (Simple Protocol for Independent Computing Environments) – remote-display system built for virtual environments by Qumranet, now Red Hat
- Splashtop – a high performance remote desktop protocol developed by Splashtop, fully optimized for hardware (H.264) including Intel / AMD chipsets, NVIDIA / ATI GPU & APU, Qualcomm Snapdragon, and NVIDIA Tegra. By optimizing for different profiles of media codecs, Splashtop can deliver high frame rates with low latency, and also low power consumption.
- Xpra – a protocol originally developed for forwarding X11 application seamlessly with audio, video, remote printing, etc. - extended to support Windows and macOS servers
- X Window System (X11) – a well-established cross-platform protocol mainly used for displaying local applications; X11 is network-transparent
Malicious variants[edit]
A remote access trojan (RAT, sometimes called creepware[4]) is a type of malware that controls a system through a remote network connection. While desktop sharing and remote administration have many legal uses, 'RAT' connotes criminal or malicious activity. A RAT is typically installed without the victim's knowledge, often as payload of a Trojan horse, and will try to hide its operation from the victim and from security software and other anti-virus software.[5][6][7][8][9][10]
Notable examples[edit]
- Bifrost[11]
- Blackshades[12][13]
- DarkComet[14][15]
See also[edit]
| Look up remote desktop in Wiktionary, the free dictionary. |
References[edit]
- ^'Remote Desktop Software'. ITarian.com. Retrieved 1 May 2019.
- ^Virtual Network Computing (VNC): Making Remote Desktop Sharing Possible. Businessnewsdaily.com (2013-11-07). Retrieved on 2014-02-27.
- ^'VMware Announces Strategic Licensing and Co-development Agreement with Teradici for True Remote PC User Experience Further Bolstering its vClient Initiative'. VMware News Releases. VMware. Retrieved 1 June 2013.
- ^'Creepware — Who's Watching You?'. Symantec Security Response. 10 December 2013.
- ^'Remote Server Administration Tools for Windows 7'. Microsoft TechNet. Microsoft. 4 June 2009. Retrieved 4 February 2011.,
- ^'Danger: Remote Access Trojans'. Microsoft TechNet. September 2002. Retrieved 5 February 2011.
- ^'Understanding the Windows NT Remote Access Service'. Microsoft TechNet. Microsoft. Retrieved 5 February 2011.
- ^'Netsh commands for remote access (ras)'. Microsoft TechNet. Microsoft. January 21, 2005. Retrieved 5 February 2011.
- ^'RAS Registry Modification Allowed Without Administrative Rights'. Microsoft TechNet. Microsoft. Retrieved 5 February 2011.
- ^'Computer RATS - Protecting Your Self'. HowTheyHack. July 2013. Archived from the original on 14 March 2016. Retrieved 17 July 2013.
- ^'Code Access Security and bifrost'. CodingHorror.com. 20 March 2007. Retrieved 5 February 2011.
- ^'BlackShades: Arrests in computer malware probe'. BBC News. Retrieved 20 May 2014.
- ^'Remarks Prepared for Delivery by Special Agent in Charge Leo Taddeo at Blackshades Press Conference'. fbi.gov. Federal Bureau of Investigation. Retrieved 20 May 2014.
- ^Denbow, Shawn. 'pest control: taming the rats'(PDF). Retrieved 5 March 2014.
- ^Aylward, Laura. 'Malware analysys - Dark Comet RAT'. Contextis. Archived from the original on 26 April 2014. Retrieved 5 March 2014.
Remote Desktop Protocol (RDP) is a sophisticated technology that uses various techniques to perfect the server's remote graphics' delivery to the client device. Depending on the use case, availability of computing resources, and network bandwidth, RDP dynamically adjusts various parameters to deliver the best user experience.

Remote Desktop Protocol multiplexes multiple Dynamic Virtual Channels (DVCs) into a single data channel sent over different network transports. There are separate DVCs for remote graphics, input, device redirection, printing, and more. Windows Virtual Desktop partners can also use their extensions that use DVC interfaces.
The amount of the data sent over RDP depends on the user activity. For example, a user may work with basic textual content for most of the session and consume minimal bandwidth, but then generate a printout of a 200-page document to the local printer. This print job will use a significant amount of network bandwidth.
When using a remote session, your network's available bandwidth dramatically impacts the quality of your experience. Different applications and display resolutions require different network configurations, so it's essential to make sure your network configuration meets your needs.
Estimating bandwidth utilization
RDP uses various compression algorithms for different types of data. The table below guides estimating of the data transfers:
| Type of Data | Direction | How to estimate |
|---|---|---|
| Remote Graphics | Session host to client | See the detailed guidelines |
| Heartbeats | Both directions | ~ 20 bytes every 5 seconds |
| Input | Client to session Host | Amount of data is based on the user activity, less than 100 bytes for most of the operations |
| File transfers | Both directions | File transfers are using bulk compression. Use .zip compression for approximation |
| Printing | Session host to client | Print job transfer depends on the driver and using bulk compression, use .zip compression for approximation |
Other scenarios can have their bandwidth requirements change depending on how you use them, such as:
- Voice or video conferencing
- Real-time communication
- Streaming 4K video
Estimating bandwidth used by remote graphics
It's tough to predict bandwidth use by the remote desktop. The user activities generate most of the remote desktop traffic. Every user is unique, and differences in their work patterns may significantly change network use.
The best way to understand bandwidth requirements is to monitor real user connections. Monitoring can be performed by the built-in performance counters or by the network equipment.
However, in many cases, you may estimate network utilization by understanding how Remote Desktop Protocol works and by analyzing your users' work patterns.
The remote protocol delivers the graphics generated by the remote server to display it on a local monitor. More specifically, it provides the desktop bitmap entirely composed on the server.While sending a desktop bitmap seems like a simple task at first approach, it requires a significant amount of resources. For example, a 1080p desktop image in its uncompressed form is about 8Mb in size. Displaying this image on the locally connected monitor with a modest screen refresh rate of 30 Hz requires bandwidth of about 237 MB/s.
To reduce the amount of data transferred over the network, RDP uses the combination of multiple techniques, including but not limited to
- Frame rate optimizations
- Screen content classification
- Content-specific codecs
- Progressive image encoding
- Client-side caching
To better understand remote graphics, consider the following:
- The richer the graphics, more bandwidth it will take
- Text, window UI elements, and solid color areas are consuming less bandwidth than anything else.
- Natural images are the most significant contributors to bandwidth use. But client-side caching helps with its reduction.
- Only changed parts of the screen are transmitted. If there are no visible updates on the screen, no updates are sent.
- Video playback and other high-frame-rate content are essentially an image slideshow. RDP dynamically uses appropriate video codecs to deliver them with the close to original frame rate. However, it's still graphics, and it's still the most significant contributor to bandwidth utilization.
- Idle time in remote desktop means no or minimal screen updates; so, network use is minimal during idle times.
- When remote desktop client window is minimized, no graphical updates are sent from the session host.
Keep in mind that the stress put on your network depends on both your app workload's output frame rate and your display resolution. If either the frame rate or display resolution increases, the bandwidth requirement will also rise. For example, a light workload with a high-resolution display requires more available bandwidth than a light workload with regular or low resolution. Different display resolutions require different available bandwidths.
The table below guides estimating of the data used by the different graphic scenarios. These numbers apply to a single monitor configuration with 1920x1080 resolution and with both default graphics mode and H.264/AVC 444 graphics mode.
| Scenario | Default mode | H.264/AVC 444 mode | Thumbnail | Description of the scenario |
|---|---|---|---|---|
| Idle | 0.3 Kbps | 0.3 Kbps | User is paused their work and there's no active screen updates | |
| Microsoft Word | 100-150 Kbps | 200-300 Kbps | User is actively working with Microsoft Word, typing, pasting graphics and switching between documents | |
| Microsoft Excel | 150-200 Kbps | 400-500 Kbps | User is actively working with Microsoft Excel, multiple cells with formulas and charts are updated simultaneously | |
| Microsoft PowerPoint | 4-4.5 Mbps | 1.6-1.8 Mbps | User is actively working with Microsoft PowerPoint, typing, pasting. User also modifying rich graphics, and using slide transition effects | |
| Web Browsing | 6-6.5 Mbps | 0.9-1 Mbps | User is actively working with a graphically rich website that contains multiple static and animated images. User scrolls the pages both horizontally and vertically | |
| Image Gallery | 3.3-3.6 Mbps | 0.7-0.8 Mbps | User is actively working with the image gallery application. browsing, zooming, resizing and rotating images | |
| Video playback | 8.5-9.5 Mbps | 2.5-2.8 Mbps | User is watching a 30 FPS video that consumes 1/2 of the screen | |
| Fullscreen Video playback | 7.5-8.5 Mbps | 2.5-3.1 Mbps | User is watching a 30 FPS video that maximized to a fullscreen |
Dynamic bandwidth allocation
Remote Desktop Protocol is a modern protocol designed to adjust to the changing network conditions dynamically.Instead of using the hard limits on bandwidth utilization, RDP uses continuous network detection that actively monitors available network bandwidth and packet round-trip time. Based on the findings, RDP dynamically selects the graphic encoding options and allocates bandwidth for device redirection and other virtual channels.
This technology allows RDP to use the full network pipe when available and rapidly back off when the network is needed for something else.RDP detects that and adjusts image quality, frame rate, or compression algorithms if other applications request the network.
Limit network bandwidth use with throttle rate
In most scenarios, there's no need to limit bandwidth utilization as limiting may affect user experience. Yet in the constrained networks you may want to limit network utilization. Another example is leased networks that are charged for the amount of traffic used.
In such cases, you could limit an RDP outbound network traffic by specifying a throttle rate in QoS Policy.
Remote Desktop Protocol For Windows 7
Note
Make sure that RDP Shortpath is enabled - throttle rate-limiting are not supported for reverse connect transport.
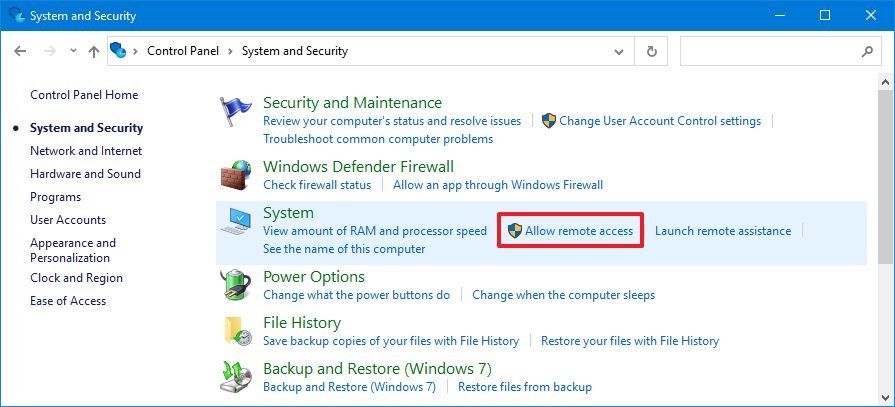
Implement throttle rate limiting on session host using Group Policy
You can use policy-based Quality of Service (QoS) within Group Policy to set the predefined throttle rate.
To create a QoS policy for domain-joined session hosts, first, sign in to a computer on which Group Policy Management has been installed. Open Group Policy Management (select Start, point to Administrative Tools, and then select Group Policy Management), and then complete the following steps:
In Group Policy Management, locate the container where the new policy should be created. For example, if all your session hosts computers are located in an OU named Session Hosts, the new policy should be created in the Session Hosts OU.
Right-click the appropriate container, and then select Create a GPO in this domain, and Link it here.
In the New GPO dialog box, type a name for the new Group Policy object in the Name box, and then select OK.
Right-click the newly created policy, and then select Edit.
In the Group Policy Management Editor, expand Computer Configuration, expand Windows Settings, right-click Policy-based QoS, and then select Create new policy.
In the Policy-based QoS dialog box, on the opening page, type a name for the new policy in the Name box. Select Specify Outbound Throttle Rate and set the required value, and then select Next.
On the next page, select Only applications with this executable name and enter the name svchost.exe, and then select Next. This setting instructs the policy to only prioritize matching traffic from the Remote Desktop Service.
On the third page, make sure that both Any source IP address and Any destination IP address are selected. Select Next. These two settings ensure that packets will be managed regardless of which computer (IP address) sent the packets and which computer (IP address) will receive the packets.
On page four, select UDP from the Select the protocol this QoS policy applies to drop-down list.
Under the heading Specify the source port number, select From this source port or range. In the accompanying text box, type 3390. Select Finish.
The new policies you've created won't take effect until Group Policy has been refreshed on your session host computers. Although Group Policy periodically refreshes on its own, you can force an immediate refresh by following these steps:
On each session host for which you want to refresh Group Policy, open a Command Prompt as administrator (Run as administrator).
At the command prompt, enter
Implement throttle rate limiting on session host using PowerShell
Remote Desktop Protocol Windows 7 Download
You can set throttle rate for RDP Shortpath using the PowerShell cmdlet below:
Next steps
Remote Desktop Protocol Download
- To learn about bandwidth requirements for Windows Virtual Desktop, see Understanding Remote Desktop Protocol (RDP) Bandwidth Requirements for Windows Virtual Desktop.
- To learn about Windows Virtual Desktop network connectivity, see Understanding Windows Virtual Desktop network connectivity.
- To get started with Quality of Service (QoS) for Windows Virtual Desktop, see Implement Quality of Service (QoS) for Windows Virtual Desktop.
