
Here’s the simple steps for you to connect to a Cisco VPN in Ubuntu 18.04 LTS.
- Cisco AnyConnect on Linux disable resolv.conf update. AnyConnect certificate/CA pinning on Cisco ASA 5510. Where to find Openldap Cisco Anyconnect schema? Cisco VPN blocks all Internet traffic and split tunneling is not permitted. Hot Network Questions Output a Latin Square.
- The information in this document is based on these software and hardware versions: ASA 5510 that runs software version 8.2(2) and ASDM version 6.4(9) Anyconnect client software version 3.0 (It will work the same for versions prior to 8.3) Microsoft.
- AnyConnect Support for Linux Cisco AnyConnect Secure Mobility Client 4.0 supports the following versions of Linux operating system: - Red Hat 6 (64-bit) - Ubuntu 12.x (64-bit).
Cisco AnyConnectは、Windows 7、8、8.1、および10、Mac OS X 10.8以降、およびLinux Intel(x64)と互換性があります。 この記事の手順に従って、Ubuntu DesktopにCisco AnyConnect VPN Mobility Clientをインストールします。この記事では、Ubuntuバージョン20.04が使用されています。.
Cisco, an American company is the leading provider and manufacturer of enterprise network devices, telecommunication hardware, networking security and networking software.
According to computer profile as of April 2018, Cisco holds a 73.9% market which makes it the undisputed leader in its industry. Without further ado here
are the steps.
1. Install vpnc and network-manager-vpnc-gnome
2. Enter your password
3. Confirm installation
4. After successfully installing the required software it is time to configure it.
5. Add a new VPN connection
6. From the VPN type options, select Cisco Compatible VPN (vpnc)
7. Enter your VPN credentials and press Add
openconnect: Connect to Cisco AnyConnect VPN
Command to display openconnect manual in Linux: $ man 8 openconnect
NAME
openconnect - Connect to Cisco AnyConnect VPN
SYNOPSIS
[
--config configfile ][
-b,--background ][
--pid-file pidfile ][
-c,--certificate cert ][
-e,--cert-expire-warning days ][
-k,--sslkey key ][
-C,--cookie cookie ][
--cookie-on-stdin ][
--compression MODE ][
-d,--deflate ][
-D,--no-deflate ][
--force-dpd interval ][
-g,--usergroup group ][
-h,--help ][
--http-auth methods ][
-i,--interface ifname ][
-l,--syslog ][
--timestamp ][
-U,--setuid user ][
--csd-user user ][
-m,--mtu mtu ][
--basemtu mtu ][
-p,--key-password pass ][
-P,--proxy proxyurl ][
--proxy-auth methods ][
--no-proxy ][
--libproxy ][
--key-password-from-fsid ][
-q,--quiet ][
-Q,--queue-len len ][
-s,--script vpnc-script ][
Anyconnect Cisco Linux
-S,--script-tun ][
-u,--user name ][
-V,--version ][
-v,--verbose ][
-x,--xmlconfig config ][
--authgroup group ][
--authenticate ][
--cookieonly ][
--printcookie ][
--cafile file ][
--disable-ipv6 ][
--dtls-ciphers  list
list ][
--dtls-local-port port ][
--dump-http-traffic ][
--no-cert-check ][
--no-system-trust ][
--pfs ][
--no-dtls ][
--no-http-keepalive ][
--no-passwd ][
--no-xmlpost ][
--non-inter ][
--passwd-on-stdin ][
--token-mode mode ][
--token-secret {secret[
,counter]|@
file} ][
--reconnect-timeout ][
--servercert sha1 ][
--useragent string ][
--os string ]
[https://]server[:port][/group]DESCRIPTION
The program
openconnectconnects to Cisco 'AnyConnect' VPN servers, which use standard TLSand DTLS protocols for data transport.
The connection happens in two phases. First there is a simple HTTPSconnection over which the user authenticates somehow - by using acertificate, or password or SecurID, etc. Having authenticated, theuser is rewarded with an HTTP cookie which can be used to make thereal VPN connection.
The second phase uses that cookie in an HTTPSCONNECTrequest, and data packets can be passed over the resultingconnection. In auxiliary headers exchanged with theCONNECTrequest, a Session-ID and Master Secret for a DTLS connection are alsoexchanged, which allows data transport over UDP to occur.
OPTIONS
--config=CONFIGFILERead further options from
CONFIGFILEbefore continuing to process options from the command line. The fileshould contain long-format options as would be accepted on the command line,but without the two leading -- dashes. Empty lines, or lines where thefirst non-space character is a # character, are ignored.
Any option except theconfigoption may be specified in the file.
-b,--backgroundContinue in background after startup--pid-file=PIDFILESave the pid toPIDFILEwhen backgrounding-c,--certificate=CERTUse SSL client certificateCERTwhich may be either a file name or, if OpenConnect has been built with an appropriateversion of GnuTLS, a PKCS#11 URL.-e,--cert-expire-warning=DAYSGive a warning when SSL client certificate hasDAYSleft before expiry-k,--sslkey=KEYUse SSL private keyKEYwhich may be either a file name or, if OpenConnect has been built with an appropriateversion of GnuTLS, a PKCS#11 URL.-C,--cookie=COOKIEUse WebVPN cookie.COOKIE--cookie-on-stdinRead cookie from standard input.-d,--deflateEnable all compression, including stateful modes. By default, only statelesscompression algorithms are enabled.-D,--no-deflateDisable all compression.--compression=MODESet compression mode, where
MODEis one of
stateless,
none, or
all.By default, only stateless compression algorithms which do not maintain statefrom one packet to the next (and which can be used on UDP transports) areenabled. By setting the mode toallstateful algorithms (currently only zlib deflate) can be enabled. Or allcompression can be disabled by setting the mode tonone.
--force-dpd=INTERVALUseINTERVALas minimum Dead Peer Detection interval for CSTP and DTLS, forcing use of DPD even when the server doesn't request it.
-g,--usergroup=GROUPUseGROUPas login UserGroup-h,--helpDisplay help text--http-auth=METHODSUse only the specified methods for HTTP authentication to a server. By default,only Negotiate, NTLM and Digest authentication are enabled. Basic authenticationis also supported but because it is insecure it must be explicitly enabled. Theargument is a comma-separated list of methods to be enabled. Note that the orderdoes not matter: OpenConnect will use Negotiate, NTLM, Digest and Basicauthentication in that order, if each is enabled, regardless of the orderspecified in the METHODS string.-i,--interface=IFNAMEUseIFNAMEfor tunnel interface-l,--syslogUse syslog for progress messages--timestampPrepend a timestamp to each progress message-U,--setuid=USERDrop privileges after connecting, to become userUSER--csd-user=USERDrop privileges during CSD (Cisco Secure Desktop) script execution.--csd-wrapper=SCRIPTRunSCRIPTinstead of the CSD (Cisco Secure Desktop) script.-m,--mtu=MTURequestMTUfrom server as the MTU of the tunnel.--basemtu=MTUIndicateMTUas the path MTU between client and server on the unencrypted network. Newerservers will automatically calculate the MTU to be used on the tunnel fromthis value.-p,--key-password=PASSProvide passphrase for certificate file, or SRK (System Root Key) PIN for TPM-P,--proxy=PROXYURLUse HTTP or SOCKS proxy for connection. A username and password can be providedin the given URL, and will be used for authentication. If authentication isrequired but no credentials are given, GSSAPI and automatic NTLM authenticationusing Samba's ntlm_auth helper tool may be attempted.--proxy-auth=METHODSUse only the specified methods for HTTP authentication to a proxy. By default,only Negotiate, NTLM and Digest authentication are enabled. Basic authenticationis also supported but because it is insecure it must be explicitly enabled. Theargument is a comma-separated list of methods to be enabled. Note that the orderdoes not matter: OpenConnect will use Negotiate, NTLM, Digest and Basicauthentication in that order, if each is enabled, regardless of the orderspecified in the METHODS string.--no-proxyDisable use of proxy--libproxyUse libproxy to configure proxy automatically (when built with libproxy support)--key-password-from-fsidPassphrase for certificate file is automatically generated from thefsidof the file system on which it is stored. Thefsidis obtained from the statvfs(2)orstatfs(2)system call, depending on the operating system. On a Linux or similar systemwith GNU coreutils, thefsidused by this option should be equal to the output of the command:stat --file-system --printf=%in $CERTIFICATEIt is not the same as the 128-bit UUID of the file system.-q,--quietLess output-Q,--queue-len=LENSet packet queue limit toLENpkts-s,--script=SCRIPTInvoke
SCRIPTto configure the network after connection. Without this, routing and nameservice are unlikely to work correctly. The script is expected to becompatible with the
vpnc-scriptwhich is shipped with the 'vpnc' VPN client. See
http://www.infradead.org/openconnect/vpnc-script.htmlfor more information. This version of OpenConnect is configured touse
/etc/vpnc/vpnc-script by default.
On Windows, a relative directory for the default script will be handled asstarting from the directory that the openconnect executable is running from,rather than the current directory. The script will be invoked with thecommand-based script host cscript.exe.
-S,--script-tunPass traffic to 'script' program over a UNIX socket, instead of to a kerneltun/tap device. This allows the VPN IP traffic to be handled entirely inuserspace, for example by a program which uses lwIP to provide SOCKS accessinto the VPN.-u,--user=NAMESet login username toNAME-V,--versionReport version number-v,--verboseMore output (may be specified multiple times for additional output)-x,--xmlconfig=CONFIGXML config file--authgroup=GROUPChoose authentication login selection--authenticateAuthenticate only, and output the information needed to make the connectiona form which can be used to set shell environment variables. When invoked withthis option, openconnect will not make the connection, but if successful willoutput something like the following to stdout:Thus, you can invoke openconnect as a non-privileged user(with access to the user's PKCS#11 tokens, etc.)for authentication, and then invoke openconnect separately to make the actualconnection as root:--cookieonlyFetch webvpn cookie only; don't connect--printcookiePrint webvpn cookie before connecting--cafile=FILECert file for server verification--disable-ipv6Do not advertise IPv6 capability to server--dtls-ciphers=LISTSet OpenSSL ciphers to support for DTLS--dtls-local-port=PORTUsePORTas the local port for DTLS datagrams--dump-http-trafficEnable verbose output of all HTTP requests and the bodies of all responsesreceived from the server.--no-cert-checkDo not require server SSL certificate to be valid. Checks will still happenand failures will cause a warning message, but the connection will continueanyway. You should not need to use this option - if your servers have SSLcertificates which are not signed by a trusted Certificate Authority, you canstill add them (or your private CA) to a local file and use that file with the--cafileoption.--no-system-trustDo not trust the system default certificate authorities. If this option isgiven, only certificate authorities given with the--cafileoption, if any, will be trusted automatically.--pfsEnforces Perfect Forward Secrecy (PFS). That ensures that if the server'slong-term key is compromised, any session keys established before the compromisewill be unaffected. If this option is provided and the server does not support PFSin the TLS channel the connection will fail.
PFS is available in Cisco ASA releases 9.1(2) and higher; a suitable ciphersuite may need to be manually enabled by the administrator using thessl encryptionsetting.
--no-dtls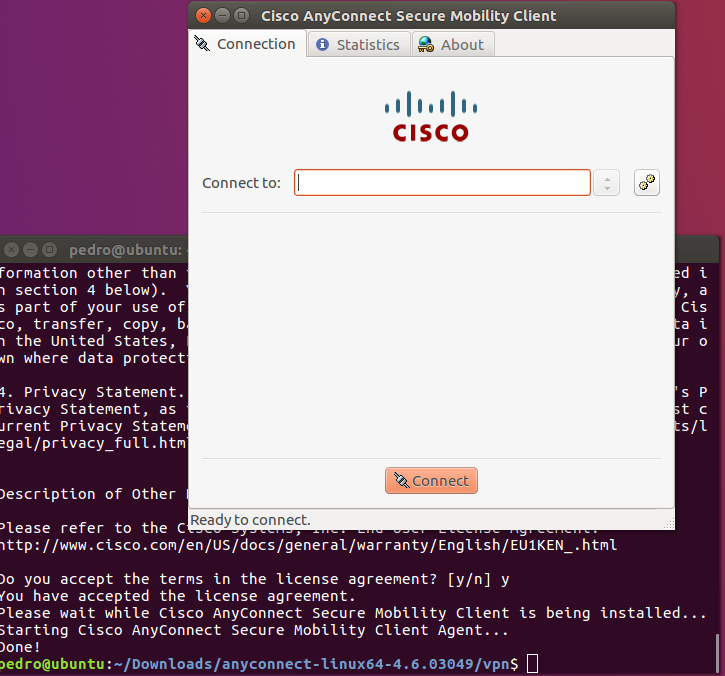 Disable DTLS--no-http-keepalive
Disable DTLS--no-http-keepaliveVersion 8.2.2.5 of the Cisco ASA software has a bug where it will forgetthe client's SSL certificate when HTTP connections are being re-used formultiple requests. So far, this has only been seen on the initial connection,where the server gives an HTTP/1.0 redirect response with an explicit
Connection: Keep-Alivedirective. OpenConnect as of v2.22 has an unconditional workaround for this,which is never to obey that directive after an HTTP/1.0 response.
However, Cisco's support team has failed to give any competentresponse to the bug report and we don't know under what othercircumstances their bug might manifest itself. So this option existsto disable ALL re-use of HTTP sessions and cause a new connection to bemade for each request. If your server seems not to be recognising yourcertificate, try this option. If it makes a difference, please reportthis information to theopenconnect-devel [at] lists.infradead.orgmailing list.
--no-passwdNever attempt password (or SecurID) authentication.--no-xmlpostDo not attempt to post an XML authentication/configuration request to theserver; use the old style GET method which was used by older clients andservers instead.
This option is a temporary safety net, to work around potentialcompatibility issues with the code which falls back to the old methodautomatically. It causes OpenConnect to behave more like olderversions (4.08 and below) did. If you find that you need to use thisoption, then you have found a bug in OpenConnect. Please seehttp://www.infradead.org/openconnect/mail.html and report this to thedevelopers.
--non-interDo not expect user input; exit if it is required.--passwd-on-stdinCisco Anyconnect For Windows 10
Read password from standard input--token-mode=MODEEnable one-time password generation using theMODEalgorithm.--token-mode=rsawill call libstoken to generate an RSA SecurID tokencode,--token-mode=totpwill call liboath to generate an RFC 6238 time-based password, and--token-mode=hotpwill call liboath to generate an RFC 4226 HMAC-based password. Yubikeytokens which generate OATH codes in hardware are supported with--token-mode=yubioath--token-secret={ SECRET[,COUNTER] | @FILENAME }The secret to use when generating one-time passwords/verification codes.Base 32-encoded TOTP/HOTP secrets can be used by specifying 'base32:' at thebeginning of the secret, and for HOTP secrets the token counter can bespecified following a comma.
RSA SecurID secrets can be specified as an Android/iPhone URI or a raw numericCTF string (with or without dashes).
For Yubikey OATH the token secret specifies the name of the credential to beused. If not provided, the first OATH credential found on the device will beused.
FILENAME,if specified, can contain any of the above strings. Or, it can contain aSecurID XML (SDTID) seed.
If this option is omitted, and --token-mode is'rsa', libstoken will try to use the software token seed saved in~/.stokenrcby the 'stoken import' command.
--reconnect-timeoutKeep reconnect attempts until so much seconds are elapsed. The defaulttimeout is 300 seconds, which means that openconnect can recoverVPN connection after a temporary network down time of 300 seconds.--servercert=SHA1Accept server's SSL certificate only if its fingerprint matchesSHA1.--useragent=STRINGUseSTRINGas 'User-Agent:' field value in HTTP header.(e.g. --useragent 'Cisco AnyConnect VPN Agent for Windows 2.2.0133')--os=STRINGOS type to report to gateway. Recognized values are:linux,linux-64,win,mac-intel,android,apple-ios.Reporting a different OS type may affect the dynamic access policy (DAP)applied to the VPN session. If the gateway requires CSD, it will also causethe corresponding CSD trojan binary to be downloaded, so you may need to use--csd-wrapperif this code is not executable on the local machine.SIGNALS
In the data phase of the connection, the following signals are handled:

 list ][ --dtls-local-port port ][ --dump-http-traffic ][ --no-cert-check ][ --no-system-trust ][ --pfs ][ --no-dtls ][ --no-http-keepalive ][ --no-passwd ][ --no-xmlpost ][ --non-inter ][ --passwd-on-stdin ][ --token-mode mode ][ --token-secret {secret[,counter]|@file} ][ --reconnect-timeout ][ --servercert sha1 ][ --useragent string ][ --os string ][https://]server[:port][/group]
list ][ --dtls-local-port port ][ --dump-http-traffic ][ --no-cert-check ][ --no-system-trust ][ --pfs ][ --no-dtls ][ --no-http-keepalive ][ --no-passwd ][ --no-xmlpost ][ --non-inter ][ --passwd-on-stdin ][ --token-mode mode ][ --token-secret {secret[,counter]|@file} ][ --reconnect-timeout ][ --servercert sha1 ][ --useragent string ][ --os string ][https://]server[:port][/group]
